Latest Posts
USB Flash drive causes the computer to restart with a blue screen. Have you ever experienced it?
Speaking of USB, many people must still remembered the severe security vulnerability of BadUSB that broke out in 2014. Hackers used this bug to transmit malicious software to the device without other people noticing, which makes all USB devices very dangerous. The most terrible thing about BadUSB is that malicious code exists in the firmware of the USB Flash driver. Since the antivirus software on PCs cannot access the area where the USB Flash stores the firmware, it means that neither antivirus software nor USB Flash format can respond to BadUSB attacks. It can only be solved by firmware update at the hardware level.

01. There are indeed many security vulnerabilities in USB devices, technicians are working to solve the problems.
Also in 2014, the WireLurker worm also broke out, and the infected computer system will indirectly infect iOS devices through the USB interface, even devices that have not been jailbroke cannot be avoided; even electronic cigarettes can spread malicious software through the USB to the PC; Later, there was a case of portable charger stealing private information from mobile phones. All this is because of the security risks from the USB protocol.

There are many USB devices in nowadays, many audio and video devices, and cameras provide USB interface. Because it is necessary to provide maximum compatibility, these devices are likely to be drive-free setting, that is, a USB device that has the characteristics of multiple input and output devices. In this way, these devices can easily be hacked. The rewritten USB Flash firmware can disguise as a USB keyboard, and the commands and codes integrated in the USB Flash firmware are input through the virtual keyboard to attack the computer, resulting in data destruction or leakage.
After the USB vulnerabilities broke out at that time, many security centers adopted improvements from the hardware level. For example, 360 wireless security research team used SecUSB, and Tencent Security Emergency Response Center used SecLine. The principle is to remove the two data lines in the USB to reduce attacks. And at the same time, users are also warned not to use untrusted USB devices to avoid infection with unknown viruses.

Despite all these problems, there are still many usage scenarios for USB. After all, the USB interface is really convenient for transmitting data. In recent years, there are more and more USB interfaces provided by the motherboard, from USB2.0 to USB3.1, and then to Thunderbolt 3 interface, there are more and more USB devices that match different interface speeds. Is this because USB devices are already safer than before? This is absolutely not the case.
Recently, a research team led by Hui Peng of Purdue University and Mathias Payer of the Swiss Federal Institute of Technology Lausanne discovered 26 new USB security vulnerabilities on different platforms through a new tool created by them, USBFuzz.
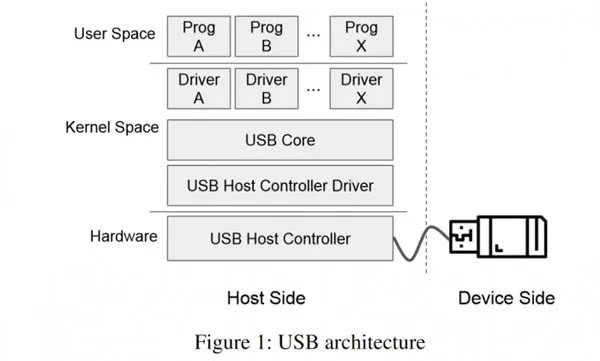
The USBFuzz tool is a new type of fuzzer specifically designed to test the USB driver stack of modern operating systems. It is a collection of multiple applications that can help security researchers input large amounts of invalid, unexpected, or random data into other applications. Afterwards, security researchers analyze the behavior of the software under test to discover new bugs, some of which may be exploited maliciously.
In the research results, Linux system has become the hardest hit area of USB security vulnerability. The research team tested USBFuzz on 9 latest versions of the Linux kernel: v4.14.81, v4.15, v4.16, v4.17, v4.18.19, v4.19, v4.19, v4.19.1, v4.19.2 and v4.20 -rc2 (latest version at the time of evaluation); FreeBSD 12 (latest version), MacOS 10.15 Catalina (latest version), and Windows (versions 8 and 10 with the latest security updates installed).
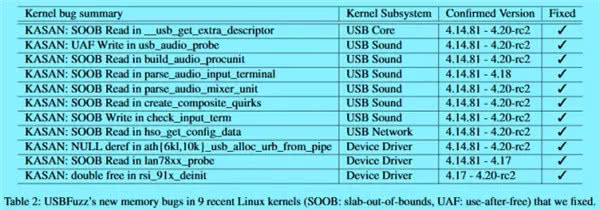
Through test, the research team found a total of 26 new vulnerabilities: three were found in MacOS, two of which caused unplanned restarts, and one caused the system to freeze; in Windows 8 and Windows 10, four vulnerabilities found can cause blue screens problems. The number of USB vulnerabilities in Linux systems has reached 18, 16 of which are high-risk memory vulnerabilities in various subsystems of Linux. In addition, 1 targets at USB in Linux, and 11 bugs have been patched.
02. USB devices must be used, safe and correct usage is very important
Seeing so many USB security vulnerabilities, should we stop using USB devices? That is definitely not possible. After all, USB devices are currently very useful in our daily work and study. Therefore, we can only avoid risks as much as possible, and use USB devices correctly and safely. Judging from the vulnerabilities discovered by this research team, the blue screen caused by USB devices must have been encountered by many people. According to a search on the Internet, there are many cases when the USB keyboards and muses cause the blue screen of the computer, and there are many cases when the USB Flash causes a blue screen or is not recognized.
From the answers of netizens, several solutions are summarized:
1. Re-download the corresponding USB driver
2. If it is caused by virus infection, it is recommended that you do not use this USB device again, in order to prevent infecting all other host devices that come into contact with this product.
3. Set the USB debugging control of the computer or mobile phone carefully.
In fact, as mentioned earlier in the article, if these USB security vulnerabilities want to be completely resolved from the USB protocol application level, we have not yet found the most ideal solution, but we can try to avoid it from the perspective of hardware and usage restrictions to prevent USB device data loss or causing other host problems.
I believe that the most common USB devices are USB Flashs and mobile hard disks, and these storage devices are also the most susceptible to be infected by viruses and carry viruses. Therefore, do not use your own storage disks frequently in printers and computers in public places. These may be untrusted devices. Regarding the problem of plugging and unplugging, most USB Flashs now support hot swap. It is recommended that you choose to safely eject the USB to exit the USB Flash to avoid damages to the files.
If you encounter problems when eject the USB mass storage device, it means that there are some writing steps in this USB Flash, you can wait for all data operations to be completed before pulling out the USB Flash. After all, this method is the only way to ensure the safe removal of the disk.
In addition to the USB disk, the USB cable is what we use most frequently in everyday life. Don’t underestimate this data line, it may lead to the loss of all your phone data. Some data cables only support charging function, while some data cables support data transmission. Therefore, when you connect the mobile phone and the computer with the data cable, you must carefully select whether turn on USB debugging function in the mobile phone or not.
Android device will pop up whether to allow debugging or not
Apple device will prompt you whether to trust the device or not
When connecting a mouse, keyboard, or even a printer with USB, make sure that it is conducted when computers are turned off instead of power-on. The wrong driver version, static electricity, etc. will cause you to power off or even burn the host when you plug in the USB interface (don’t think this is just to scare you. The USB data cable has burned the host twice in the editing office).
Not only the aforementioned USB devices, but also network cameras, cameras, etc. are now connected to other devices through the USB interface. Consumers don’t have to worry too much if they don’t know if there is a security hole in this device. We use too many USB devices in our daily life. In addition to recommend that you always back up the important data of the USB device, you should also use the USB device correctly and use the safest way to plug and unplug the device.
If you encounter problems caused by USB devices other than the above-mentioned ones, please share your solutions in the comment area to help more people effectively avoid these security risks.





Leave a comment